One of the significant challenges that consumers face today is the ever-growing threat of cybercrime. According to Cybersecurity Ventures, cybercrime is projected to cost the world $9 trillion in 2024. How will this expected cost…
Microsoft 365 continuously evolves to bring their customers the highest performing applications. All are aimed at boosting productivity, security, and company-wide synergy. Microsoft is a top choice for businesses for it’s features geared towards bettering…
Server Migration: Does Your Business Need It? A server migration is the process of moving large amounts of critical information from one server to another. This also involves making sure the new server is properly…
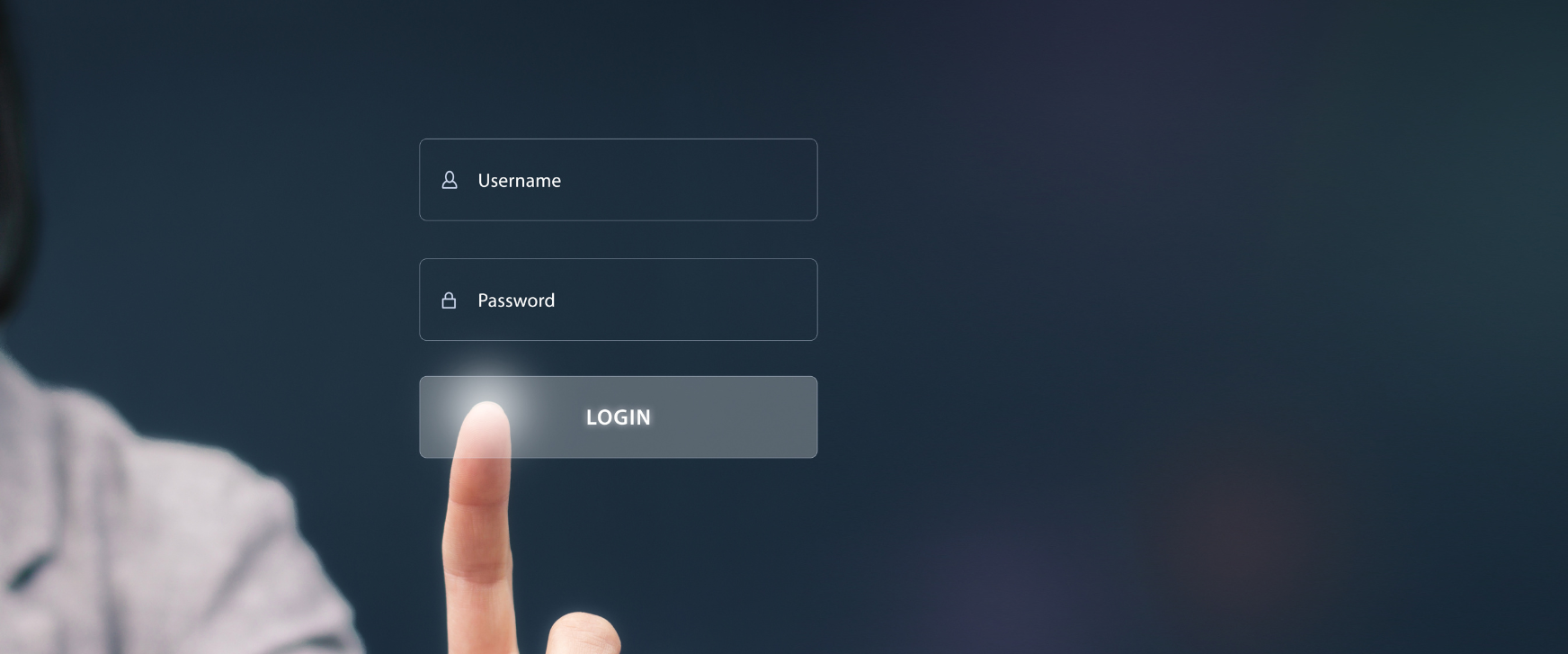
Credential stuffing is one of the latest tactics that cybercriminals are employing to exploit vulnerabilities and gain unauthorized access to your personal information. Let’s take a look at what it is, and how you can…
The “unofficial-official” shopping season starts this week, and if there is a sale, there might be a scam close by. As the prices go down, so does our guard. We fear losing out on a deal…
Phishing scams have become increasingly sophisticated and prevalent. One form that has gained traction is text phishing, or “smishing” (SMS phishing). This involves sending fraudulent text messages with the intent to deceive individuals into revealing…
For most of us, IT is a vague term to encompass all things “technology”. We trust our IT provider or in-house IT staff to keep our personal and professional data safe while on our company’s…
Many IT providers utilize an auto-answering system. While these might be convenient, it can often be frustrating or hurtful to the client’s productivity. Some of the reasons IT support is important are listed below. 1….
Responding quickly to clients is an essential part of being a company’s trusted IT provider. A slow response can lead to prolonged downtime, harm business continuity and even increase security risks. So why aren’t they…
Switching your managed service provider (MSP) can be a significant decision for your business. If you’re unsure whether it’s time to make the switch, here are 5 signs that might indicate you should consider finding…